Rationale¶
Rationale¶
This document provides the justification and objective of this GitHub repository and its contents. It outlines how it addresses various threats and how to adjust your expectations for different scenarios and environments. It also supplies lots of useful additional resources.
This repository currently has 2 main products. ![]()
Let's explore each of them in detail below
 Harden Windows Security Module¶
Harden Windows Security Module¶
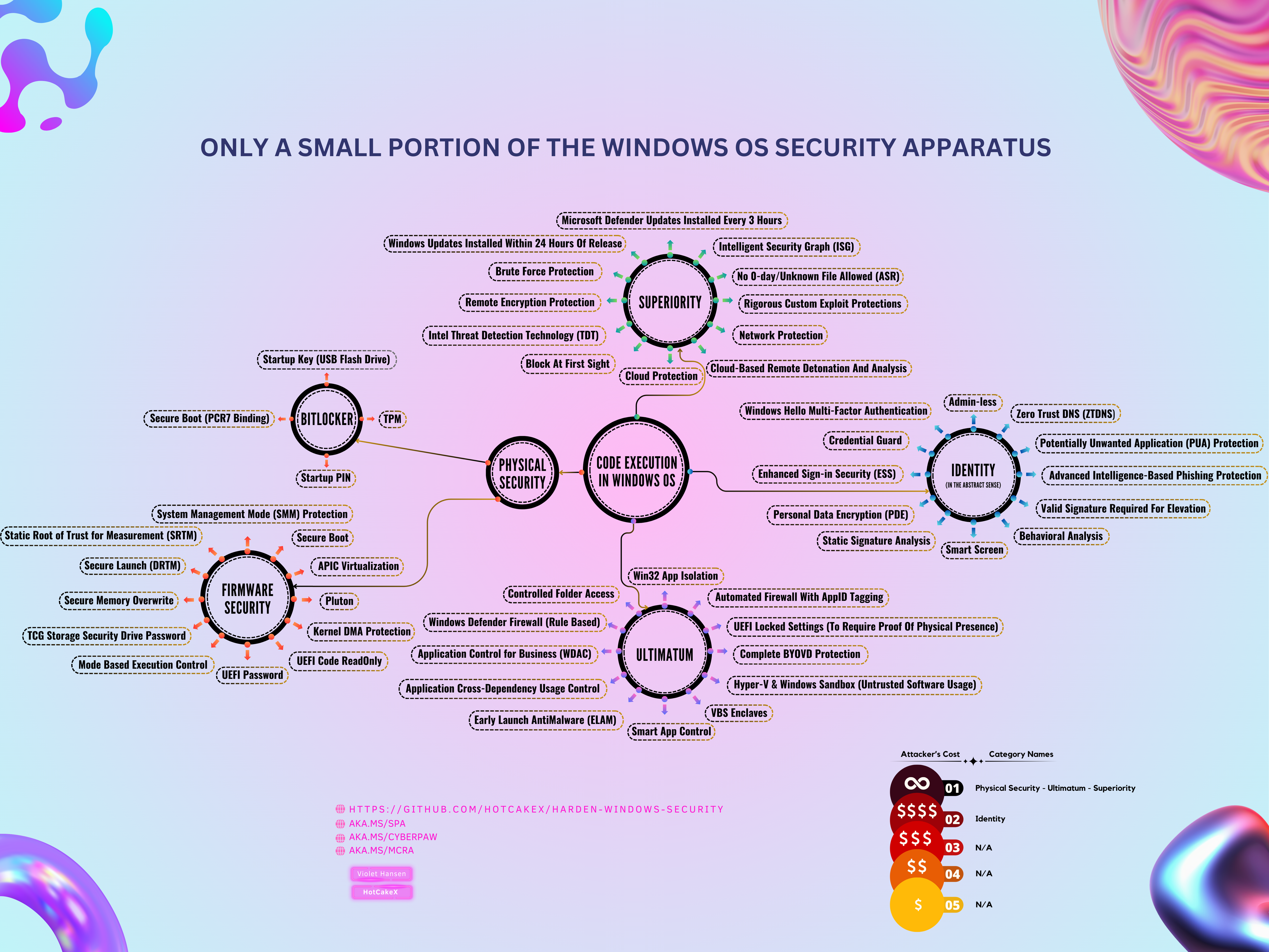
Use the Harden Windows Security module to secure your personal and enterprise devices against the majority of advanced threats. The module is suitable to be used by everyone.
If you are a personal user, you can use the Harden Windows Security to harden your Operation System, remove unnecessary features, apps and so on, check its security score or undo the hardening measures.
If you are an enterprise user or admin, you can use the provided Intune security policies from this repository and apply them from your Intune Portal to all of your workstations using Microsoft Graph API. You can then use the module to verify the compliance of the workstations against the applied policies and receive a security score.
It uses the same security features built into your device and Windows operating system to fine-tune it towards the highest security and locked-down state. It does not install any outside components and does not increase your attack surface at all.
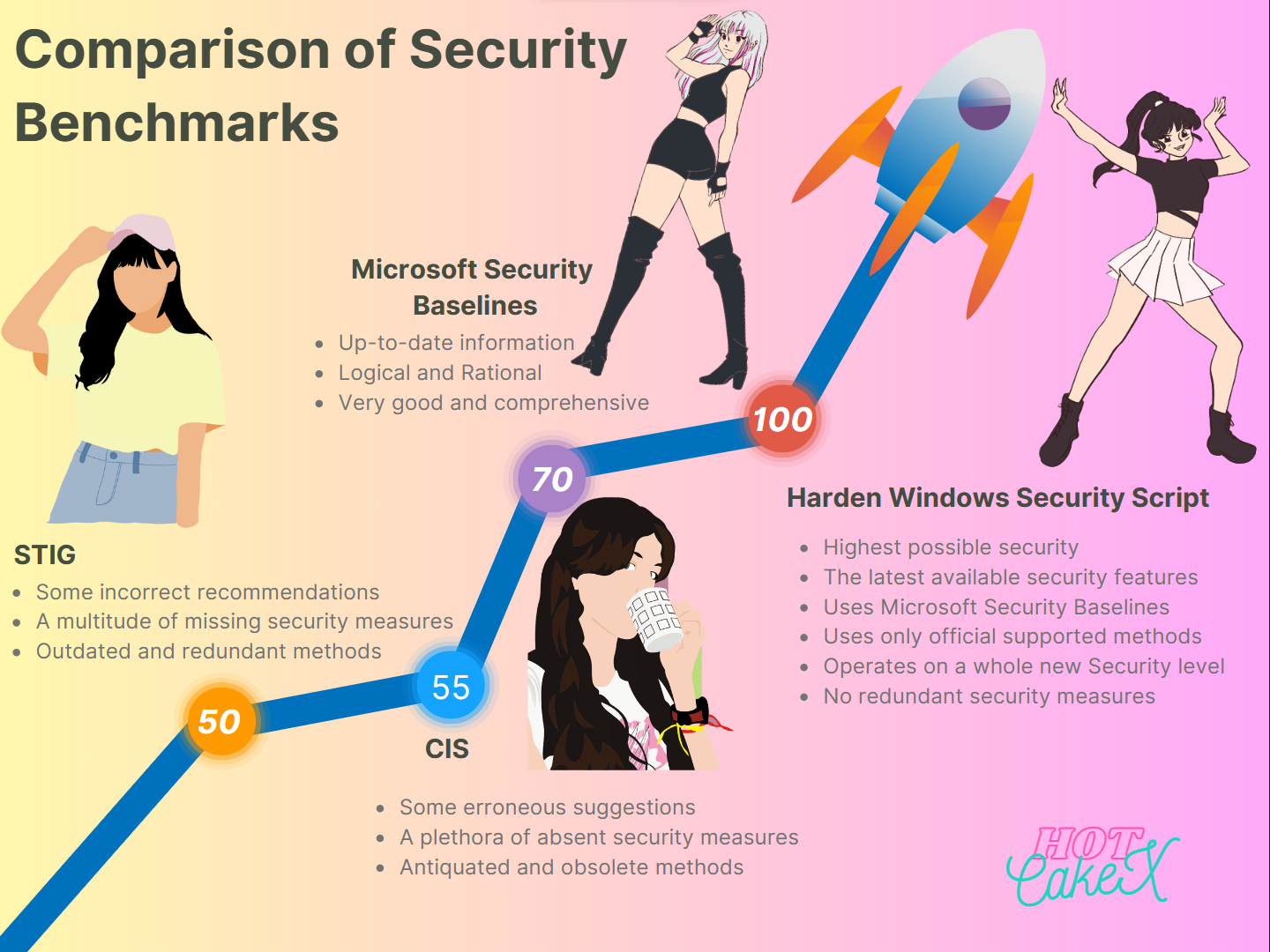
Let's Take a look at the infographics below:
 AppControl Manager¶
AppControl Manager¶
AppControl Manager is a secure open-source Windows application designed to help you easily configure Application Control in your system. It is suitable for both personal users as well as enterprises, businesses and highly secure workstations.
Tip
If you aren't familiar with what App Control is, please refer to this article where it's explained in great detail.
Proper usage of Application Control, when coupled with the Harden Windows Security module's policies, can provide 99% protection from various threats, either from the Internet or physical. It's true that there is no absolute security, but then again there is nothing absolute in the universe either. Everything, even the most fundamental physical laws, are and have been subject to change and conditions.
 How Do You Make the Right Choice?¶
How Do You Make the Right Choice?¶
First use the Harden Windows Security Module to apply the hardening measures described in the Readme. After applying these hardening measures, your system will be secure against at least ~98% of the threats when you use Standard (non-Privileged) account for everyday work. These threats aren't the usual computer viruses, they are motivated nation state threat actors.
If you want even more security and control, you have at least 2 more options:¶
-
you can either use Smart App Control, which deploys an automatic and AI based App Control policy that uses Intelligent Security Graph to authorize safe and reputable applications and files and blocks unknown and malicious files.
-
Use AppControl Manager to deploy an App Control policy and have even more control over the operation of the Windows Application Control.
These methods will create multiple layers of security; also known as defense in depth. Additionally, you can create Kernel-level Zero-Trust strategy for your system.
If there will ever be a zero-day vulnerability in one or even some of the security layers at the same time, there will still be enough layers left to protect your device. It's practically impossible to penetrate all of them at once.
Also, zero-day vulnerabilities are patched quickly, so keeping your device and OS up to date, regardless of what OS you use, is one of the most basic security recommendations and best practices you must follow.
 Vulnerabilities Such as Zero-Days Are Disclosed in 3 Different Ways¶
Vulnerabilities Such as Zero-Days Are Disclosed in 3 Different Ways¶
-
The vulnerability is disclosed responsibly. It is first communicated privately with the software vendor/developer so they can have the time to fix and issue updates/patches for the vulnerability before it is disclosed publicly. In this way, people are always safe because all that's needed is to keep your OS and software up to date to receive the latest security patches.
-
The vulnerability is disclosed irresponsibly. It is disclosed publicly, through social media or by creating PoCs (Proof of Concept) so that it can be used and abused by everyone.
-
The vulnerability is abused by malicious actors. It is exploited by threat actors in cyber attacks and privately. These vulnerabilities are either discovered by the threat actors themselves or bought from security researchers who find them first, all of which is illegal and has consequences.
 What About More Advanced Security at Scale ?¶
What About More Advanced Security at Scale ?¶
To achieve the Highest level of Security at Scale for Businesses, Enterprises and Military scenarios, you can use the following services to create impenetrable devices and environments.
Important
The following services must be used in addition to the measures already talked about in this repository, such as proper Application Control policies and the security measures that the Harden Windows Security module applies. They are not a replacement for them.
As an individual user you can still utilize these features and services, they add an additional layer of protection to your security stack.
-
Microsoft Defender for Endpoint - Discover and secure endpoint devices across your multiplatform enterprise.
-
Microsoft Security Copilot - Build a defense so automated that even your intern becomes a cybersecurity expert.
-
Confidential Computing on Azure - Protect your highly sensitive data while it's in use
-
Confidential AI - Train your data Privately and Securely on the most advanced AI Super computers
-
Microsoft Entra conditional access - Increase protection without compromising productivity
-
Microsoft Sentinel - Scalable, cloud-native solution that provides SIEM, SOAR and more!
-
Key Vault - Safeguard cryptographic keys and other secrets used by cloud apps and services. This Azure service uses the best products in the world for the job, such as Thales HSMs. More info available here.
-
Microsoft Defender for Cloud - Protect multicloud and hybrid environments with integrated security from code to cloud
-
Microsoft Defender for Cloud Apps - Modernize how you secure your apps, protect your data, and elevate your app posture with software as a service (SaaS) security.
-
Microsoft Defender for Identity - Protect your on-premises identities with cloud-powered intelligence.
-
Passwordless authentication options for Azure Active Directory - Multifactor and Passwordless Authentication, the most secure and convenient way of authentication.
-
PIM (PAM) - Privileged Access Management
-
PAW - Privileged Access Workstation
-
SAW - Secure Admin Workstations
-
List of all Azure security services for Enterprises, Businesses etc.
 Important Considerations¶
Important Considerations¶
-
Avoid using any 3rd party security solutions when using Harden Windows Security module or App Control for Business. 3rd party solutions are weak, incompatible and unnecessary, they also increase your attack surface.
-
Use Virtual machines for any questionable or unsafe software. Use Windows Sandbox or Hyper-V VM. Also consider using Virtual machines or Microsoft Defender Application Guard (MDAG) for browsing on highly secure workstations.
 Which Device to Use ?¶
Which Device to Use ?¶
Use Microsoft Surface products for the best device and firmware security. They support secured-core PC specifications, the manufacturing process and platform is trusted and secure.
Make sure to use Surface products that support Device Firmware Configuration Interface (DFCI) for extra protection and security. Here is a list of Surface products that support it.
-
How to use Device Firmware Configuration Interface (DFCI) for Surface Devices with Intune
-
Among other features, devices set up with DFCI can be set that boot from USB device(s) is disabled and there is no way to bypass the chip level security directly, not even CMOS clear can bypass it, because it uses non-volatile memory aka flash storage. It sets BIOS cert authentication, and the private key is behind the cloud edge inside Intune and not even Microsoft support can get that key.
-
The list of Surface products supporting DFCI might not get updated quickly in that doc but fear not, this is an active project and all new surface devices have this built in, the docs team might be just a little laggy.
-
Microsoft Surface devices use Project Mu for the source code of their firmware.
-
Surface devices can use certificates instead of password for UEFI. They don't have a reset switch like other devices either. You create and install your own certificate using Surface Management Toolkit. You can build a config package that has the certificate in it and install it to the firmware, then the package can't be removed or changed without the signing cert authorizing the change, aka, cert auth, or you can just use DFCI as previously mentioned and not have to worry because the packages are signed with MS's private key and there is no PKI that you have to self host.
-
Business class Surface devices have dedicated TPM chips.
-
Check out the Device Guard category about Secured-Core specifications.
-
Pluton security chip is not a requirement for Secured-Core certification.
-
Pluton security chip is included in Qualcomm Snapdragon ARM CPUs, AMD and Intel CPUs.
-
Copilot+ PCs are among the most secure consumer grade devices. They are secured-core and incorporate the Pluton security chip.
Important
![]() It is important to be aware of potential hardware backdoors that may compromise the security of your system. Some common OEMs, such as Compaq, Dell, Fujitsu, Hewlett-Packard (HP), Sony, and Samsung, with OEMs that use unmodified Insyde H20, or Phoenix firmwares utilize algorithms based on device serial numbers for password resets. These algorithms allow for master password removal from the firmware, potentially granting unauthorized access to the system.
It is important to be aware of potential hardware backdoors that may compromise the security of your system. Some common OEMs, such as Compaq, Dell, Fujitsu, Hewlett-Packard (HP), Sony, and Samsung, with OEMs that use unmodified Insyde H20, or Phoenix firmwares utilize algorithms based on device serial numbers for password resets. These algorithms allow for master password removal from the firmware, potentially granting unauthorized access to the system.
Note
![]() When buying 3rd party devices, make sure they have the Pluton security chip, it addresses security needs like booting an operating system securely even against firmware threats and storing sensitive data safely even against physical attacks.
When buying 3rd party devices, make sure they have the Pluton security chip, it addresses security needs like booting an operating system securely even against firmware threats and storing sensitive data safely even against physical attacks.
 Protection against BYOVD (Bring Your Own Vulnerable Driver) attacks¶
Protection against BYOVD (Bring Your Own Vulnerable Driver) attacks¶
-
Secured core PCs provide the hardware that is capable of protecting against BYOVD attacks. It is your responsibility to turn the features on, those include App Control for Business, ASR (Attack Surface Reduction) rules, Dynamic/static root of trust and firmware that is extensible for revoking drivers. They are specially useful for drivers not explicitly mentioned in the Microsoft Recommended Driver Block List, which are the more dynamic side of things.
-
Use Strict Kernel-mode App Control policy for complete BYOVD protection
 What to Do When There Is an Attack ?¶
What to Do When There Is an Attack ?¶
You should have an existing Unified Contract with Microsoft (formerly known as Premier Support). Microsoft offers a wide range of services and teams to help you recover from a cyber attack such as:
- GHOST: Global Hunting, Oversight and Strategic Triage
- DART - The Microsoft Detection and Response Team
- CRSP - Global Compromise Recovery Security Practice Team - including Ransomware
After you've got hacked, you should request them by contacting your Customer Success Account Manager and telling them you need the help of one of these teams.
Tip
When getting cyber security insurance for your company or organization, make sure to get one that covers the cost of hiring Microsoft's elite teams such as GHOST/DART, i.e. those Microsoft teams will be in-network for your insurance.
Color breakdown of security teams in organizations¶
- 🔴 Red - Pen Testers/White Hat Hackers
- 🔵 Blue - SOC/Data Science/Telemetry Analysis/SIEM Junkies
- 🟢 Green - Fixers, takes input from blue and red and builds the fixes that are needed for identified blind spots (blue) or vulnerability/risk (red)
- 🟡 Yellow - Tooling, SWE to build new stuff for all of the above to operate faster and more effectively
 For Penetration testing and benchmarking¶
For Penetration testing and benchmarking¶
How to properly perform a pentest and benchmark a system hardened by this repository and make it as close to a real-world scenario as possible:
- Use a physical machine if possible, it should have Windows 11 certified hardware, Standard user account.
-
If you can't use a physical machine, use Hyper-V hypervisor. Your host (aka physical machine) must have Windows 11 certified hardware and meet all the hardware and UEFI security requirements explained in the Readme. VMs however are prone to side channel attacks, so don't use that attack vector in pentests if you want more realistic results.
-
First apply the Harden Windows Security module (All categories of it) and then use the AppControl Manager to deploy a suitable Signed App Control policy.
Important
Always Pay attention to the Microsoft Security Servicing Criteria for Windows, specially the Security boundaries. There is no security boundary between Administrator to Kernel.
Some penetration testers overlook this fact, assuming it is a vulnerability that they can perform administrative tasks such as disabling security features as Administrator. This is an expected behavior. Administrators have the power to control the security of a device and can disable security features at their discretion. This is why you need to use a Standard user account when performing a realistic penetration test.
Another aspect to consider is the ambiguity in the word "Admin". There are at least two distinct types of Admins: Local Admin and Cloud Admin. For instance, when you are penetration testing a system that leverages enterprise cloud security solution such as Microsoft Defender for Endpoint (MDE), Admin access should be regarded as Cloud Admin since those devices use Microsoft Entra ID and lack Local Admin. In this situation, Cloud Admin can effortlessly disable security features as expected, rendering a pentest using Local Admin access utterly pointless. Conversely, when pentesting a system that only relies on personal security features such as Microsoft Defender, then Admin should be treated as Local Admin. In this case, the Admin can also disable any security feature for the same reasons stated above.
Of course, Microsoft employs additional security measures such as Protected Process Light (PPL) for Defense in Depth strategies, but they do not alter the facts stated above. The goal is to always hope for the best, plan for the worst.
 Any questions or suggestions?¶
Any questions or suggestions?¶
Please open a new issue or discussion in the repository.